Following the release of our report, The Scandinavian HR-IT Report 2020, we recently ran a webinar that explored current access management and data security concerns. Our guest speakers were Ole Tom Seierstad, National Security Officer at Microsoft, and Arne Bergesen, Manager Architects at Crayon.
If you missed the live webinar, you can of course stream the recording for free on our website, but if you’d like to take a quick overview of the many critical topics covered, we’ve summarised them for you here.

Moving to the cloud with confidence
The COVID-19 crisis has driven the digital revolution forward at a much faster pace than some organisations were ready for. Suddenly, working from the cloud isn’t just something you could plan to adopt in the next year or two, it needs to happen now. But along with this knowledge comes many valid security concerns. How can you be sure your organisational and employee data is secure, compliant with privacy laws, and accessible for everyone who needs it? And, of course it should be absolutely inaccessible to those who shouldn’t be anywhere near it!
Today, in our self-service world, we need to make sure employees and customers have access to the resources and intelligence that every business offers in one way or another, from wherever they are, and the only way to achieve this is via the cloud. Digital is becoming the preferred choice for many, many interactions, especially when working remotely, social distancing and practicing safety guidelines in relation to virus prevention.
This means almost every business is asking themselves if the cloud is the right place to be. According to Ole Tom Seierstad, the answer is yes, but only with the right investment in people, tools, and adequate security measures. The security landscape is changing quickly, and it’s essential to choose service providers that can keep up with these changes.
Understanding the threats
The top two blockers that prevent businesses from moving to the cloud are security and privacy compliance, especially concerning data stored outside the EU, and the higher security requirements needed to properly deploy cloud solutions. No one is saying the cloud isn’t right for their organisation anymore, but many are rightly concerned about how to adopt and implement cloud solutions responsibly.
The top cyber security threat actors today are:
- Cyber criminals (financially motivated)
- Nation-state (espionage motives)
- Hacktivists (politically motivated)
- Insiders (opportunists within your organisation)
This last group is not as widely known or protected against as they should be, Seierstad noted. However, the motivations aside, the tools are the same no matter the actor. These attack vectors are:
- Social engineering
- Phishing
- Identity spoofing
- Malware
- Supply chain insertion
- Man-in-the-middle
- Denial of service (DoS) attacks
All of these attacks are about people; namely, they are about tricking or luring people into acting irresponsibly. It is estimated that it only takes from one to two days from the first infiltration to a bad actor taking full control of your network. And, once inside, it can be very difficult to detect and remove them.
Prevention is the best cure
Your identity is the new key to your office—your virtual office, anyway. Access should only be granted when the system is absolutely sure you are who it thinks you are. That used to mean strong passwords, but passwords are one of the biggest security issues organisations are faced with today. Think about the fact that if you don’t have a password, i.e. you can gain access in other, more secure ways, there is nothing for an attacker to steal.
This means taking on extra measures such as 2-factor authentication, biometrics, Single Sign On, and so forth.
Cloud concerns
Before moving to the cloud, you should find out: Is your data safe in the provider’s data centre? Who has access to your content in this service? What visibility into your content’s activity do you have? Is the data flow encrypted so the service provider can’t see it?
Here is a look at the Microsoft model for conditional access:
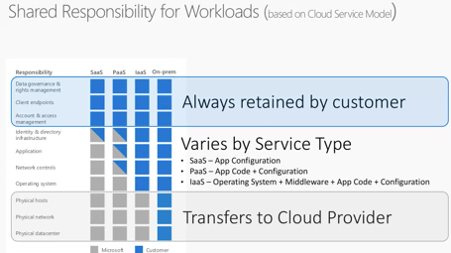
Here you can see the differing responsibilities for different service types, and how you benefit from the security measures offered by a cloud provider without sacrificing data privacy or the management of your access rights.
You should also make sure your cloud provider has the certifications you expect, is compliant with applicable regulations, and offers appropriate encryption of data, both when it is stored and when it is traveling between devices or users. Request details of any audits or certificates and ask what guarantees are in place. There is no such thing as too much data security.
According to Arne Bergesen from Crayon, when you move to a secure cloud solution and use it to take stock of your security performance, you may begin to find errors and flaws in your data security and quality. This is not because there are more errors, but rather because it is easier to find them. This enables you to monitor and analyse your data, making auditing easier, clarifying your performance, and assisting your business with transparency.
Identity management is at the core of access security
There is no point using identity for access and security if you don’t have a good system to manage identifying data. Mid-to-large sized companies have, on average, up to fifty different IT solutions that their employees need differing levels of access to, some with multiple roles. Without a system to handle onboarding, offboarding and internal movement, the licensing costs and risk of security breaches can spiral out of control. It’s incredibly difficult – and time-consuming – to manage this manually; what you need is an HR system that maintains master data quality and that can automate many of these processes. This is where CatalystOne can help.
For more detailed information on moving to the cloud, how cloud security works, and how an HR system can manage your master data, watch our on-demand webinar.
If you’d like to see the CatalystOne system in action, or would like to talk to one of our consultants, you can book a demo with us.

